SQL injection in harvard subdomain
Hi. In this writeup, i will show you a sqli that i found in harvard and also, a xss as a bonus
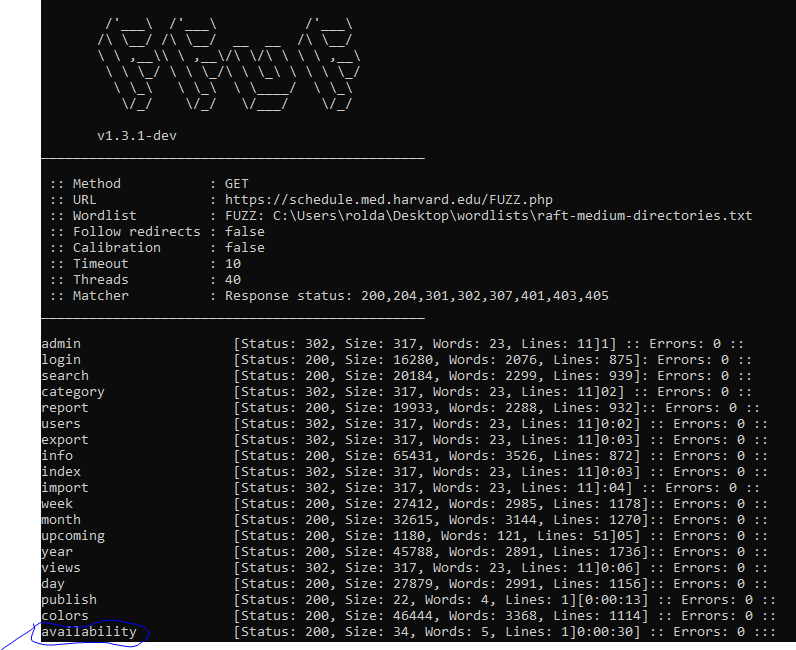
While looking through the subdomains of harvard, i found this one interesting subdomain https://schedule.med.harvard.edu/ . I fuzzed the directory using ffuf and found this one interesting endpoint availability.php
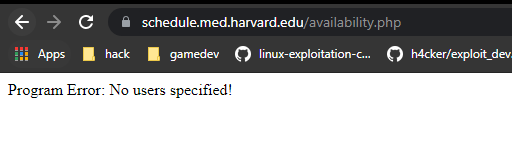
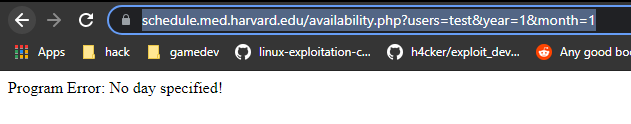
Visiting that endpoint only gave me this.
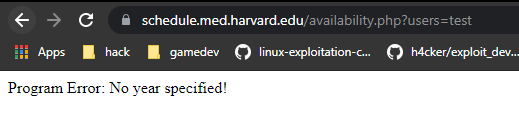
So i fuzzed the parameters using arjun and found an interesting parameter called users. I tried it again with the users parameter and saw this
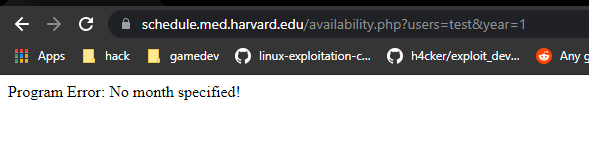
This is the same error message as before. So i guessed i only have to provide a year parameter. I did that and it worked.
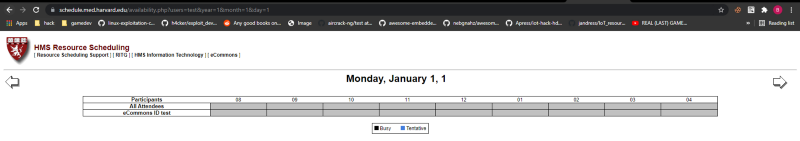
Again, its the same as before, i provided a month parameter and it worked.
It worked again, but now, its asking for a day parameter, i gave it and it showed me this
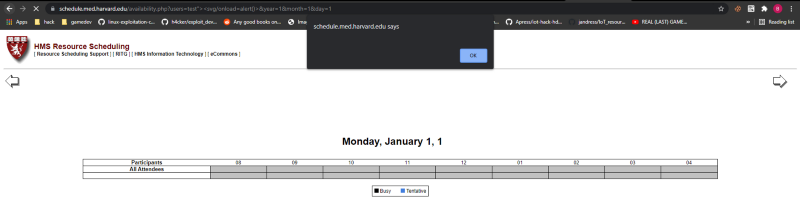
We can see that our input in users parameter is reflected so i tried to get an xss. And it worked
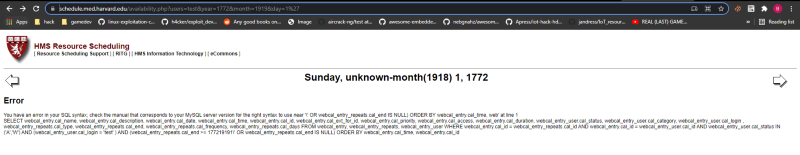
So we have an xss. I quickly reported it and tried testing the other parameters. I tried adding ‘ in the day parameter and it gave me an sql error.
So, i have an sqli injection here. Since i suck at sql injection, i just let sqlmap do the job for me and sqlmap worked.
I dumped the tables. I didnt go any further anymore and reported it to them.
The sqli got accepted but the xss does not. Apparently, harvard dont accept xss which sucks since i reported alot of xss to them
This is now fixed so i decided to publish it. Visiting the subdomain will show this
And visiting the endpoint https://schedule.med.harvard.edu/availability.php will throw a 404 error.
Thats the end of the writeup, thanks for reading.